Software and hardware migrations happen. They should not result in the loss of information potentially relevant to known or reasonably anticipated legal matters. The Secret Service says that they ‘lost’ text data from January 5-6, 2021 in a long planned “system migration”. While it now appears that some or all of the lost texts may be recovered and produced, the failure of preservation process has already damaged the reputation of the Secret Service. What would happen to the stock price of a corporation accused of deliberately ‘losing’ key records in a high publicity investigation?
I frequently support and certify corporate client migrations that involve records under legal hold. Most of these are massive enterprise archives or PST-to-M365 migrations. Some data loss from malformed/encrypted content is inevitable. My recommended defensibility strategy includes:
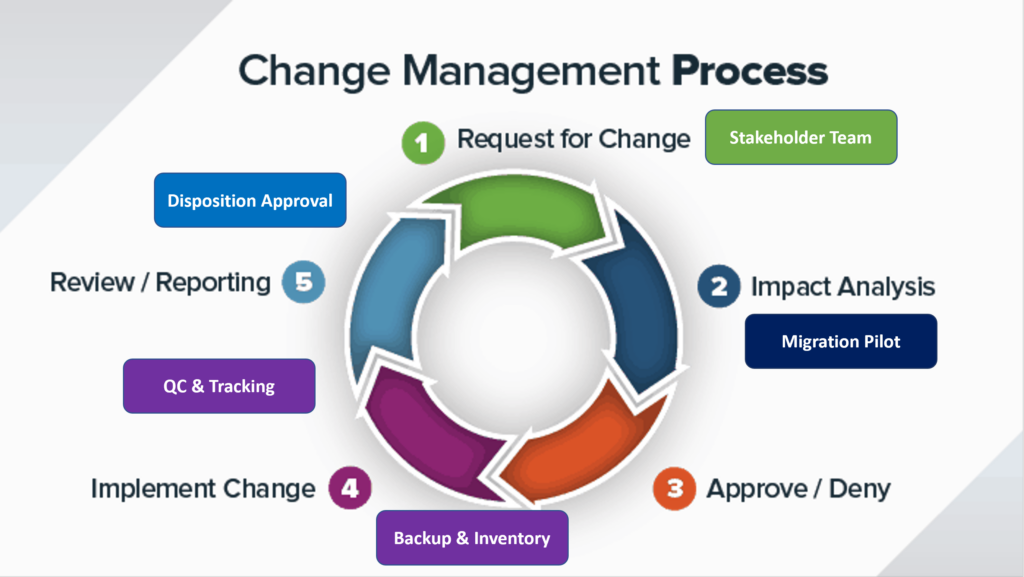
- Communication – Notification and recruitment of key stakeholders.
- Documentation – Define the scope, configuration and proposed migration plan.
- Assess Impact -Identify potential holds impacted, get stakeholder/legal decisions on reasonable effort/risk questions.
- Inaccessible Preservation – Determine practicality, effort and cost of making selective or system wide backups for long term offline preservation. I prefer to limit these to hold scope where possible.
- Migration Pilot –Sample set of custodians, locations, departments and compare migrated content to identify any metadata or content that is altered or lost. Dates and ownership metadata should be carefully checked. Pilot users should be actively engaged to identify any loss of functionality or hidden issues.
- Finalize Plan – Assuming the pilot results are acceptable, the team should approve the final workflow that includes last good backups, cut over date(s) and other details that minimize loss and data duplication.
- Legacy Inventory – Run item level reports (where possible) for quality control and defensible remediation events.
- Tracking – Migrations can take months and typically go in waves to minimize user impact. Some migration platforms do a good job tracking this while more manual IT driven migrations will require detailed daily logs.
- Live QC – I always recommend a 3rd party expert or team conduct live metric and content checks on waves to catch issues in process. Did the number of migrated items match to the inventory counts? Does sample item content, attachments and metadata match or map to the new system?
- Migrated Inventory – Where possible run item level reports to be compared to the pre-migration inventory.
- Final QC – System wide metrics comparisons provide assurance that there was no systematic data loss or provide a remediation map. This usually requires database crunching rather than giant spreadsheets and a technical resource.
- Final Report – The full metrics, cost, time and QC results should be presented to stakeholders for final approval.
- Decommissioning – Whether this was a system or device migration, the legacy containers/content should be either preserved offline (tapes, redundant drive arrays, cloud, etc.) or properly disposed of based on the risk/impact assessment.
If the Secret Service had followed a similar process, the ‘lost’ phones would have been identified as under hold before the migration. The phones inarguably contained records and potential classified communications that many bad actors would have sought. How is it that their migration plan did not include verified backups prior to migration? How could any responsible agency counsel not reasonably expect discovery requests for phones?
So how can corporate counsel control risk of ongoing migrations? Regular communication and coordination between IT, legal, security, HR and other compliance related teams is critical. I encourage clients to conduct annual/quarterly roadmap and status meetings to create visibility across corporate siloes. All of this is an expansion of basic change management lifecycle to accommodate preservation requirements. Does your IT team have the ability to see or search active hold scopes? If not, is there an established compliance approval in your change management workflow?
Mobile devices are a moving target in eDiscovery preservation, collection and content review. Mobile discovery tools typically lag behind evolving phone, mobile content and user innovation. We need more tools like ModeOne or methods to synchronize mobile content to repositories with eDiscovery functionality such as OneDrive.
Greg Buckles wants your feedback, questions or project inquiries at Greg@eDJGroupInc.com. Contact him directly for a free 15 minute ‘Good Karma’ call if he has availability. He solves problems and creates eDiscovery solutions for enterprise and law firm clients.
Greg’s blog perspectives are personal opinions and should not be interpreted as a professional judgment or advice. Greg is no longer a journalist and all perspectives are based on best public information. Blog content is neither approved nor reviewed by any providers prior to being published. Do you want to share your own perspective? Greg is looking for practical, professional informative perspectives free of marketing fluff, hidden agendas or personal/product bias. Outside blogs will clearly indicate the author, company and any relevant affiliations.
Want to see my pandemic project? Visit KnowNow to explore how eDiscovery tools can be applied on your own data to create a personal knowledge management system. Apply for early access while you can!
See Greg’s latest pic on Instagram.